AWS Cognito Service
With Amazon Cognito, you can add user sign-up and sign-in features and control access to your web and mobile applications.
Amazon Cognito provides an identity store that scales to millions of users, supports social and enterprise identity federation, and offers advanced security features to protect your consumers and business. Built on open identity standards, Amazon Cognito supports various compliance regulations and integrates with frontend and backend development resources.

AWS Cognito Access Token
If you’re using Amazon Cognito to manage user authentication in your application, you should be aware of the permissions users have by default when issued an access token.
When signing into an application that uses Amazon Cognito for authentication, the following three tokens are returned to the user: an ID token, an access token, and a refresh token. The assigned scope defines the token’s access level for the particular user.
When the token scope is set to “aws.cognito.signin.user.admin” the user has the permission to view and edit their user attributes stored within Cognito (e.g., username, email, custom attributes, etc.).

Please note that the “aws.cognito.signin.user.admin” is the default scope when creating a user pool, and it’s commonly seen in implementations.
Privilege Escalation Using AWS Cognito Custom Attributes
Privilege escalation in web applications refers to the process in which a potential attacker[PB1] [MM2] [PB3] gains higher levels of access or control within the application than they were originally granted. This can occur through a variety of methods, such as exploiting vulnerabilities in the application code, taking advantage of weak authentication mechanisms, or bypassing access control mechanisms.
There are two main types of privilege escalation in web applications: vertical and horizontal.
Changing AWS Cognito custom attributes could potentially be used to facilitate either vertical or horizontal privilege escalation.
For example, if a user is able to modify their own custom attributes in a way that grants them higher privileges or permissions, this could be a form of vertical privilege escalation.
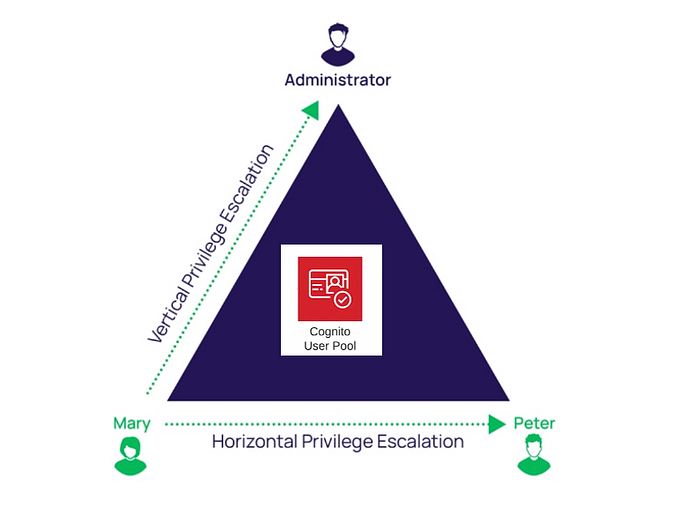
Vertical privilege escalation occurs when a user gains access to a higher level of privileges or permissions than they were originally granted, for example from standard user to admin.
In the context of AWS Cognito, a user might be able to escalate their privileges horizontally by gaining access from a normal user account to an administrative account user or group by editing custom attribute custom:isAdmin:false to custom:isAdmin:true, or any other custom attribute that referrers to vertical privileges.
Horizontal privilege escalation, on the other hand, occurs when a user gains access to resources or data that they were not authorized to access within their current level of privileges.
In the context of AWS Cognito, a user might be able to escalate their privileges horizontally by gaining access to data or resources belonging to another user or group.
In this example, the user has the custom attribute of organization ID in a way that grants them access to resources or data of that organization; if we change this attribute, it is a form of horizontal privilege escalation.

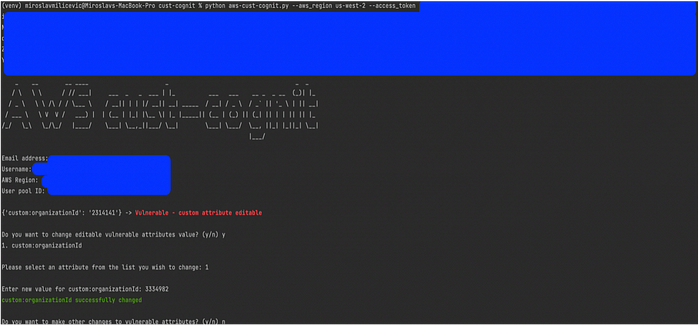
Exploitation Tool — aws-cust-cognit
aws-cust-cognit is an exploitation tool designed to test the security level of AWS Cognito user accounts.
It allows users to identify and exploit vulnerabilities in user accounts by checking for custom attributes that can be changed to escalate privileges.
Tool setup:
git clone https://github.com/UN1QUELY/aws-cust-cognit
cd aws-cust-cognit
pip install -r requirements.txt
Usage:
python aws-cust-cognit.py — aws_region <aws-region> — access_token <access-token>
Exploitation Process
· Log into the web application using AWS Cognito and intercept the request via a proxy, such as Burp Suite

· Copy access token and region
· python aws-cust-cognit — access_token <access_token> — region us-west2